Fill out the form and choose SOC Solution from the drop-down menu
Experience comprehensive security oversight with our integrated SIEM and SOC services. Our solutions enhance threat detection, streamline incident response, and fortify your cyber defenses for ultimate peace of mind.
Fill out the form and choose SOC Solution from the drop-down menu
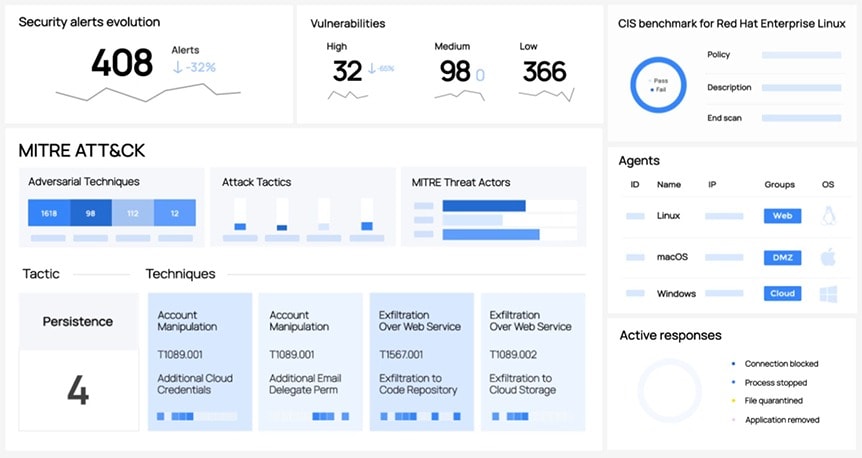
SIEM software consolidates, analyzes, and aids in the monitoring of security data, enhancing your ability to detect cyber threats across your IT landscape.
SIEM provides real-time visibility into your network’s security, streamlines compliance reporting, and helps identify anomalies for swift threat resolution.
A Security Operations Center is your dedicated team monitoring your network around the clock, ready to respond to security incidents at a moment’s notice.
SOC services offer continuous surveillance, expert incident handling, and strategic security advisement, bolstering your organizational resilience against cyber attacks.
Integrate and orchestrate security monitoring with our SIEM-SOC solutions for unparalleled threat detection, streamlined response, and improved compliance management.
24/7 surveillance across networks, ensuring constant security vigilance and immediate detection of suspicious activities.
Automated alerting mechanisms that promptly notify your security team of potential threats, facilitating quick action.
Efficient consolidation and analysis of logs from multiple sources, providing a unified view of security events.
Access to up-to-date threat data that informs your security measures, allowing you to anticipate and counteract threats.
Efficient consolidation and analysis of logs from multiple sources, providing a unified view of security events.
Empower your IT and operations with our SIEM solution. Keep your network and endpoints free from disruptions.
Our SIEM integrates with most cloud and productivity platforms while following industry compliance. Integrations include Microsoft Azure, Google Cloud, Amazon Web Services, and Microsoft Office 365.








Our SIEM follows industry standards and covers a variety of advanced threat detection and Malware removal tools to protect your applications and networks at all times.